
The U.S. Cybersecurity and Infrastructure Security Agency, (CISA) states that quantum computers cannot break public key encryption algorithms. However, both public and private entities must be prepared for possible future attacks against cryptography that’s not resistant to quantum. Most of today’s digital communications, including cryptocurrencies, leverage public key encryption and CISA believes when “quantum computers reach higher levels of computing power and speed, they will be capable of breaking the public key cryptography algorithms that are in use today.”
The US government warns nation-states that private companies are actively pursuing quantum computing methods that could threaten current cryptographic standards
Modern encryption methods could soon be used to break cryptocurrencies. That’s according to a recent CISA report published at the end of August. In the report, the U.S. government agency stresses that it is essential to transition to postquantum cryptography. “Do not wait until the quantum computers are in use by our adversaries to act,” CISA’s report details. “Early preparations will ensure a smooth migration to the post-quantum cryptography standard once it is available.”
The debate about quantum computing’s ability to crack public key encryption has been ongoing since 1998 when scientists worked together to entangle the first qubits (quantum bits). Quantum computers utilize intricate physics in order to calculate powerful equations related to today’s contemporary crypto and mathematical systems. The super quantum computer has improved since 1998. There are now 14 calcium-ion qubits that were entangled in 2011, 16 superconducting quebits for 2018, and 18 entangled qubits for 2018. CISA believes quantum computers can create new opportunities, but they also have negative implications for encryption security.
“Nation-states and private companies are actively pursuing the capabilities of quantum computers,” CISA’s report details. “Quantum computing opens up exciting new possibilities; however, the consequences of this new technology include threats to the current cryptographic standards.”
While Researchers Say Bitcoin’s Public Key Technology Leverages ‘Multiple Quantum-Resistant One-Way Hash Functions,’ Some Blockchain Projects Prepare for a Post-Quantum World
Cryptocurrencies like Bitcoin leverage contemporary encryption methods and it has been said many times over the years that there’s a need to protect cryptocurrencies with post-quantum encryption. In 2020, when the industrial firm Honeywell revealed it built a quantum computer that effectively leverages six effective qubits, crypto supporters started discussing quantum computers’ potential future effects on Bitcoin and 256-bit encryption. Some supporters of crypto currency have started to plan for a quantum-computer encryption-breaking event. Cambridge Quantum Computing is in the midst of working with Honeywell on a project that “can be applied to any blockchain network.”
Some researchers believe that large-scale quantum computers won’t come to pass despite the best efforts of cryptographers. Some scientists believe the timeframe is closer than we expect, and some have suggested it may take five years. According to the National Institute of Standards and Technology, 15 years seems more realistic. Meanwhile, Ethereum developers have been researching quantum resistance alongside the Hyperledger Foundation’s distributed ledger project Ursa. Preparing for a postquantum world, cryptographers believe encryption techniques such as AES-128 (or RSA-2048) will not be sufficient to protect against quantum computer attacks.
Andreas Antonopoulos: ‘Satoshi Nakamoto’s Little Genius Design Element Is Not an Accident’
The debate has raged on for years and many people think the government’s warnings and the recent quantum-based technological achievements by Honeywell, Google, Microsoft, and others, are the incentives people need to embrace post-quantum cryptography.
Numerous articles, reports, and mainstream headlines assert that quantum computing will be able to break existing encryption and forecast accidents and traffic jams well in advance. However, Bitcoin proponents have said on various occasions that the SHA256 encryption employed by Satoshi’s creation is a formidable foe against a post-quantum world.
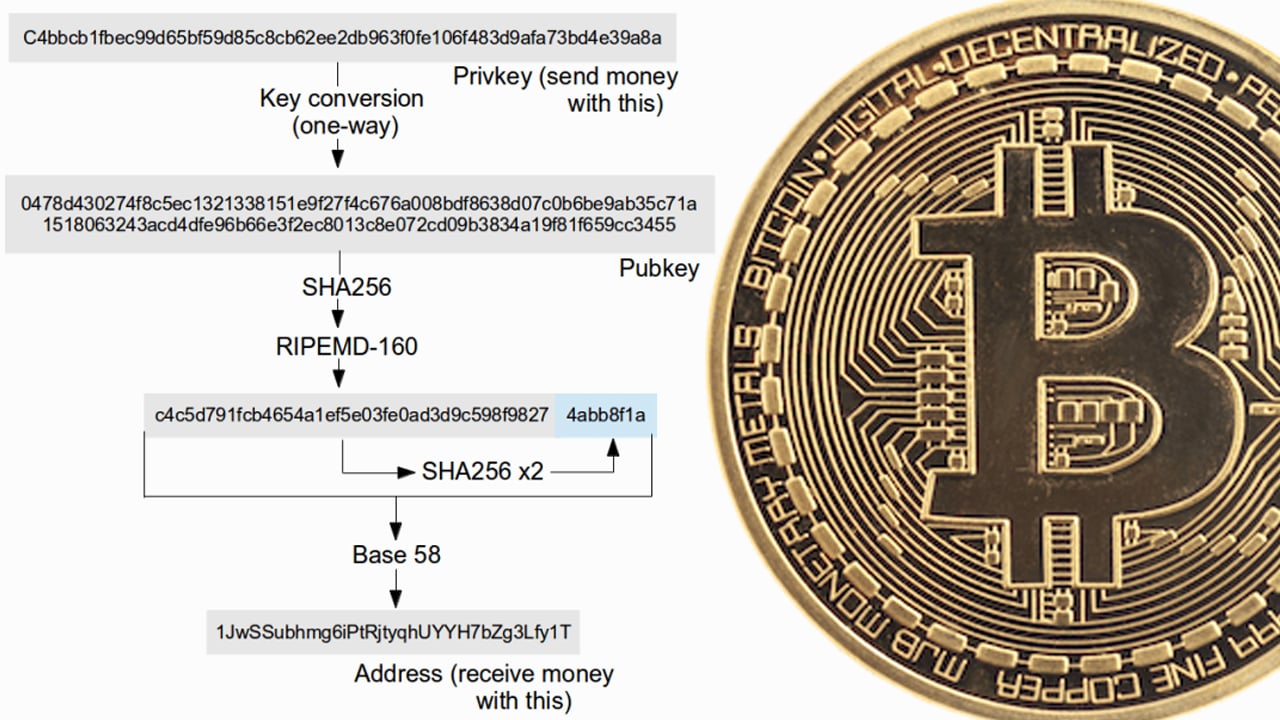
“In Bitcoin your public key isn’t (initially) made public. While you share your bitcoin address with others so that they can send you bitcoins, your bitcoin address is only a hash of your public key, not the public key itself,” software developer and cryptocurrency proponent Chris PaciaIn 2014, wrote “What does that mean in English? A hash function can be described as a one-way cryptographic function which takes input data and converts it to cryptographic output. By one-way, I mean that you can’t derive the input from the output. It’s kind of like encrypting something [and] then losing the key.”
The software developer’s 2014 paper on the subject concludes:
All of that is a complicated way of saying that while an attacker with a quantum computer could derive the private key from the public key, he couldn’t derive the public key from the bitcoin address since the public key was run through multiple quantum-resistant one-way hash functions.
Video featuring the bitcoin evangelist Andreas AntonopoulosAccording to him, using multiple bitcoin addresses at different times is crucial for bitcoin security. Antonopoulos stressed that Satoshi’s two cryptography design choices are “absolutely genius.” “What you use, which is a Bitcoin address, is a double-hashed version of your public key — which means that the public key is never seen by anyone until you claim it by spending the transaction … This little genius design element is not an accident,” Antonopoulos further said in his keynote speech. “What it does is, it creates a second layer abstraction of the underlying cryptographic algorithm used in elliptic curve digital signatures allowing you to do future upgrades.”
Antonopoulos continued:
This means the past is protected because it’s hidden behind the second veil. The future is also possible because an address can be presented that does not have an elliptic or other curve. Or, an algorithm can be used to create a quantum-resistant signing algorithm. So, you can do forwards modification to secure the future, and you’ve got backwards protection because you have hid the past.
What do you think about the U.S. government’s recent warning about quantum computers? Comment below and let us know how you feel about the subject.
Images CreditsShutterstock. Pixabay. Wiki. Commons. Chris Pacia. Bitcoin Not Bombs.
DisclaimerThis article serves informational purposes. It does not constitute an offer, solicitation, or recommendation of any company, products or services. Bitcoin.com is not a provider of investment, tax, legal or accounting advice. The author and the company are not responsible for any loss or damage caused by the content or use of any goods, services, or information mentioned in the article.